Hi, I'm Jingjing Wang .
A
Self-driven, quick starter, passionate for solving a complex and challenging real-world problems.
About
I am a undergraduate student of Zhejiang University major in Information Security. I enjoy problem-solving and coding and believe that the most important thing is to enjoy the process but not the end. I have worked on technologies like Python, MySQL, C, C++, Verilog, Chisel, Riscv and Mips during my first three school years. I am passionate about diving into complex problems and fully enjoy the process to think , explore and handle. I'm always on the way finding what I truly love and strive to bring 100% to the work I do.
- Languages: Python, C, C++, Bash, Verilog, Chisel
- Databases: MySQL
- Libraries: NumPy, Pandas, Matplotlib
- Frameworks: Qt, PyTorch
- Tools & Technologies: Git, Docker, Qemu, Verilator
Projects
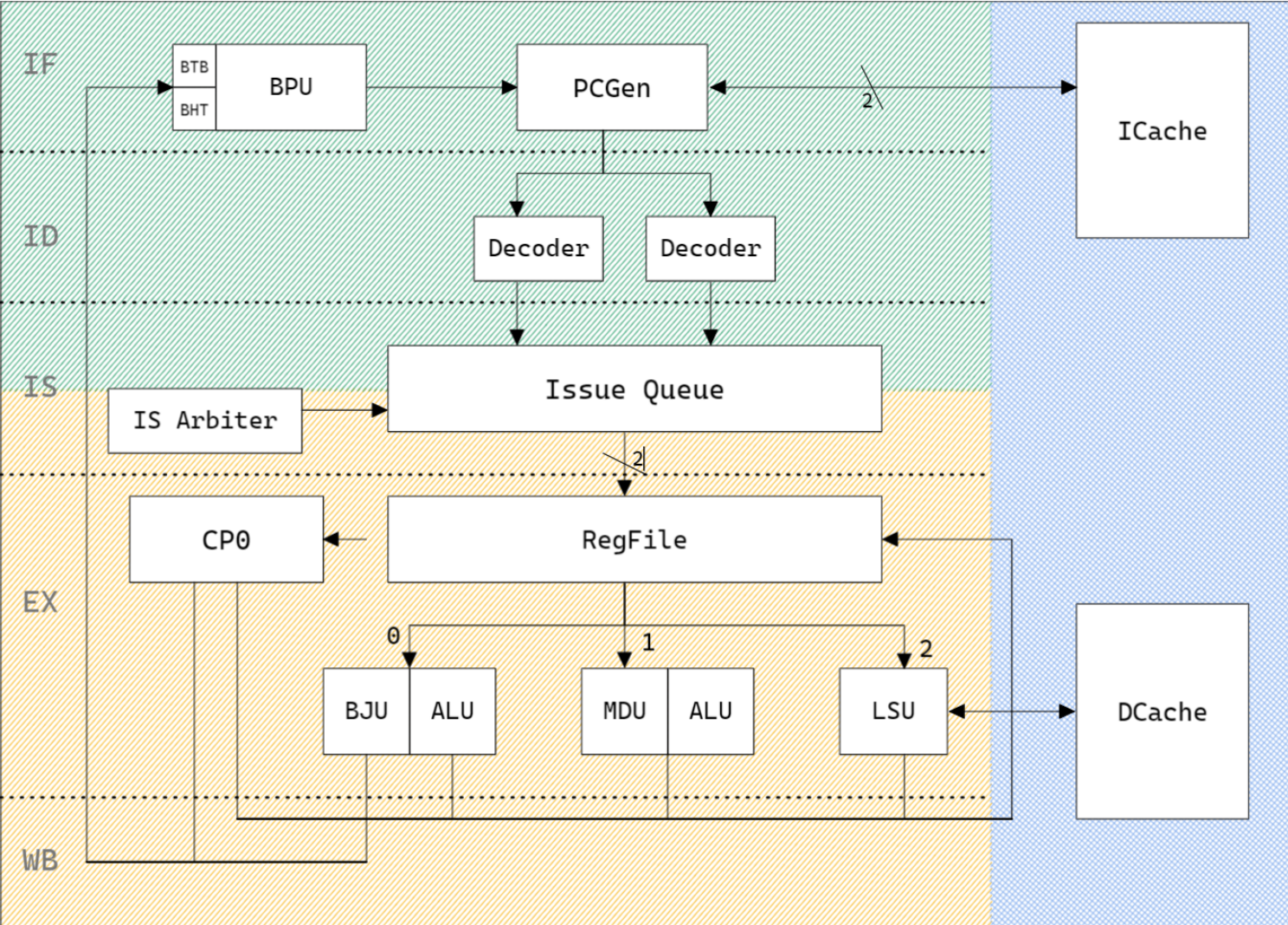
A five-stage pipeline Mips32 CPU based on Chisel
- Award: NSCSCC2022 group second prize
- Tools: Chisel, Verilog, Qemu, Verilator
- Sequential dual-issue five-stage pipeline, 110MHz time frequency.
- Branch prediction based on BHT and BTB with 88.24% prediction accuracy.
- QMC (Quine-McCluskey) minimalize the logic of decoder.
- Pipeline Cache read and write.
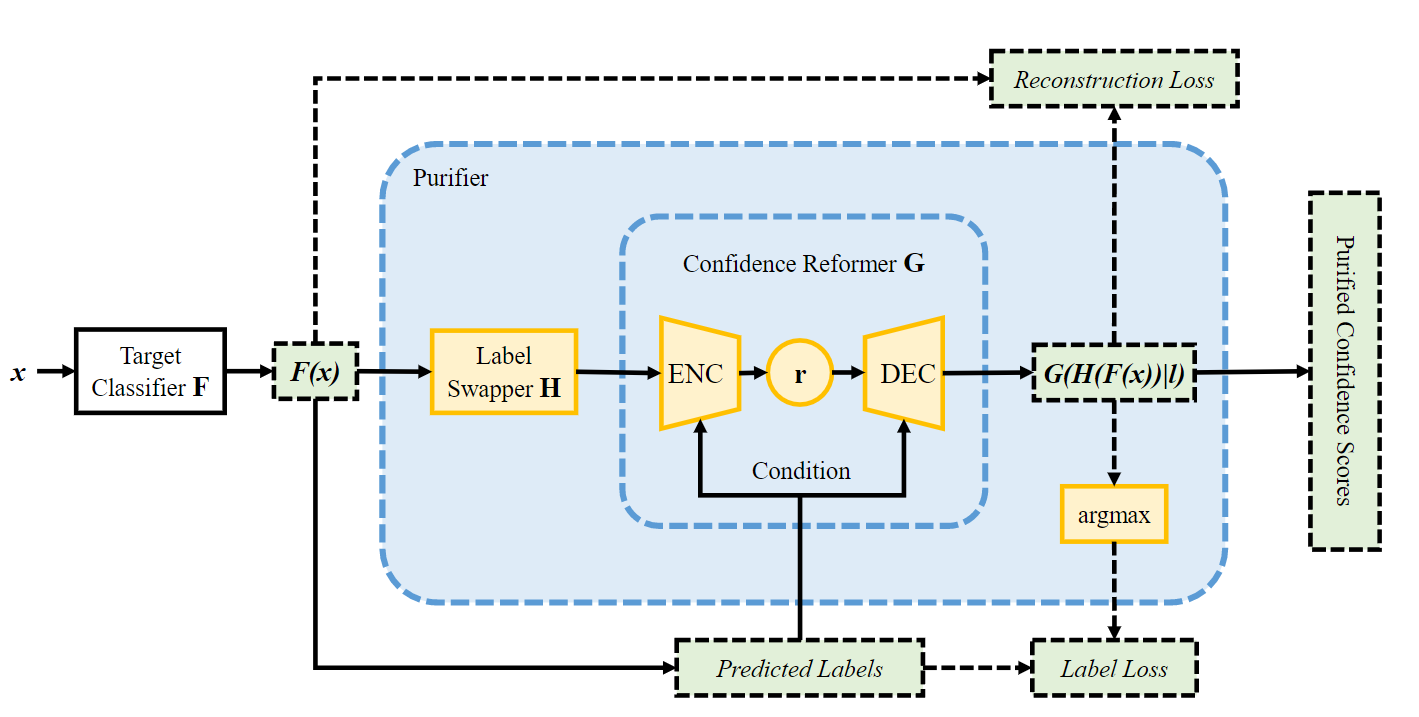
A defense method against Data Inference in Deep Learning
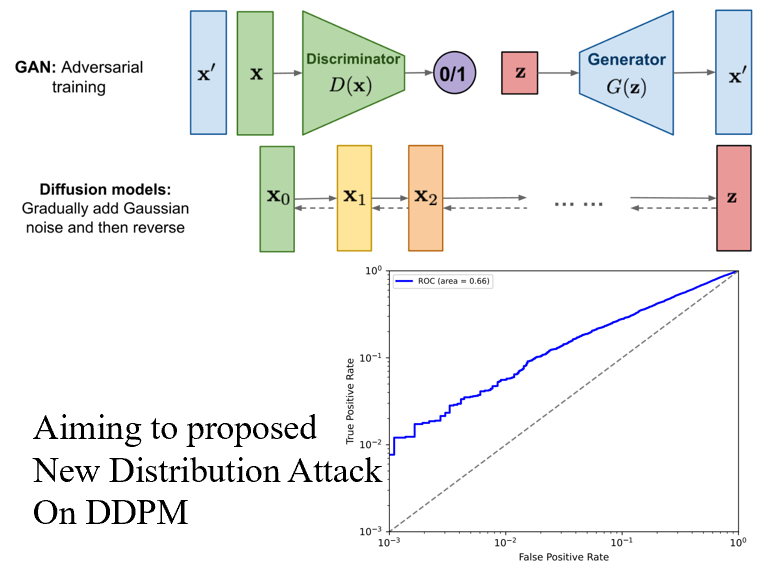
Distribution Inference Attack against Generative Models
- Aiming: CCS underreview
- Tools: Python, Pytorch, Matplotlib
- Whether the newly populated diffusion model or the classic GAN, they'll leak training information beyond comprehension.
- We work on the granularity of data distribution or what we say class feature, aiming at proposing a more general attack.
Skills
Languages and Databases
 Python
Python
 MySQL
MySQL
 Chisel
Chisel
 Shell Scripting
Shell Scripting
 C++
C++
Libraries
 NumPy
NumPy
 Pandas
Pandas
 matplotlib
matplotlib
 pwntools
pwntools
Frameworks
 PyTorch
PyTorch
 QT
QT
Other
 Git
Git
 Qemu
Qemu
 Docker
Docker
 Verilator
Verilator
 CodeQL
CodeQL
Education
Hangzhou, Zhejiang, China
Major: Information Security, College of Computer and Science
GPA: 4.73/5.0 (3.99/4.0)
Rank: 2/723 (Information category of engineering for first semester), 1/27 (Information Security for following semesters)
English: CET4-588, CET6-593
- Advanced/Basic Data Structures and Algorithms
- Computer Organizations(Logic Design, Computer Architectures, Operating System)
- Database
- Computer Network
- Software Security, Encryptography, Computer Network Security Theory and Practice
- Corporate Finance, Microeconomics, Macroeconomics
Relevant Courseworks: